Since Emails are sent as plain text messages, encrypting and signing them is crucial. Anybody sniffing the connection traffic on routes used to deliver the message could have a look at your private e-mails or manipulate contents without having to open any envelope. Therefore, this tutorial is about encrypting your e-mails using PGP (= Pretty Good Privacy). This cipher is 100% proof against cracking attempts if the key is chosen well. This tutorial can be used with any popular email account like Yahoo! Mail, G-Mail, GMX, Web.de, etc. You will not have any costs for encrypting your e-mails pretty good ;) . This way you are also able to create unique signatures for e-mails, files, etc. This way, users can ensure the authenticity of a received e-mail.
(As follows, I am using Screenshots of the German tutorial - this will be updated - you are welcome to submit appropriate screenshots by email)
time of exposure : 20 - 40 minutes
Software used : - GnuPG
- Enigmail is gonna be installed by the package manager of your Linux distribution
- K-Mail
For most distributions, there are up-to-date packages:
Debian/Ubuntu :
apt-get install thunderbird
apt-get install enigmail
Gentoo (you need to activate the crypt USEflag locally in /etc/portage/package.use or globally in /etc/portage/make.conf to install Enigmail Support) :
emerge thunderbird
or with a temporary activated crypt USEflag
USE=crypt emerge --ask --verbose thunderbird
Fedora :
yum install thunderbird
yum install thunderbird-enigmail
there are also Sources and Binaries located at Mozilla FTP
1.2 KDE Users should give K-Mail a try:
Debian/Ubuntu :
apt-get install k-mail
Gentoo :
emerge k-mail
Fedora :
yum install k-mail
Linux:
apt-get install gnupg
Gentoo :
emerge gnupg
Fedora :
yum install gnupg
type gpg --gen-key:
gpg --gen-key
following dialogue will show up:
(1) RSA and RSA (default)(2) DSA and Elgamal(3) DSA (sign only)(4) RSA (sign only)
choose (1)
RSA keys may be between 1024 and 4096 bits long. What key size do you want? (2048)
I recommend 4096 Bits, default is 2048 Bits.
Please specify how long the key should be valid.0 = key does not expire= key expires in n daysw = key expires in n weeksm = key expires in n monthsy = key expires in n yearsKey is valid for? (0)
Choose 1 Year : 1y
Please specify how long the key should be valid.Real Name:
give your name as it is shown with your email-address
Email address:
It is important to give the correct E-Mail Address! The comment part is obligatory and can be skipped.
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit?
type in O and press Enter.
You should create a revokation certificate to revoke your keys if your private key ever should get compromised.
To list all keys you got you can do as follows:
Public Keys:
gpg -k
Private Keys:
gpg -K
To create your revocation certificate, simply give following command and save it @ some external storage to keep it save:
gpg --gen-revoke deine@email.com > deine@email.com-revoke.crt
You should also back up your key pairs along with your revoke crt, if you need to reinstall your system or use them on different machines.
Export all private keys:
gpg --export-secret-keys --armor > secret.keys
NEVER SHARE YOUR PRIVATE KEY!!! If this happens by accident just generate a new keypair!
Export all public keys:
gpg --export --armor > public.keys
Export a single public key :
gpg --export --armor youremail@address > youremail@address.key
To send encrypted e-mails to some friend of yours, you have to import his public key and sign it as trusted:
Following example is using this public key.
gpg --import admin@geebee.org.pub
gpg --edit-key admin@geebee.org
gpg> trust
pub4096R/9CF1F408created: 2013-11-15expires: 2014-11-15usage: SCtrust: validity: [ultimate] (1). geeBee UG (haftungsbeschränkt) <admin@geebee.org>Please decide how far you trust this user to correctly verify other users' keys(by looking at passports, checking fingerprints from different sources, etc.)1 = I don't know or won't say2 = I do NOT trust3 = I trust marginally4 = I trust fully5 = I trust ultimatelym = back to the main menuYour decision? 5Do you really want to set this key to ultimate trust? (y/N) ypub4096R/9CF1F408created: 2013-11-15expires: 2014-11-15usage: SCtrust: ultimatevalidity: ultimate
quit
You can use this key pair with any mail client supporting PGP encryption as K-Mail, Thunderbird, Sylpheed, Clawsmail or Balsa.
2.1.1 Setting up a Thunderbird Email Account:
First we click at E-Mail to create a new account.
Following dialog also opens up when we fire up Firebird the first time -
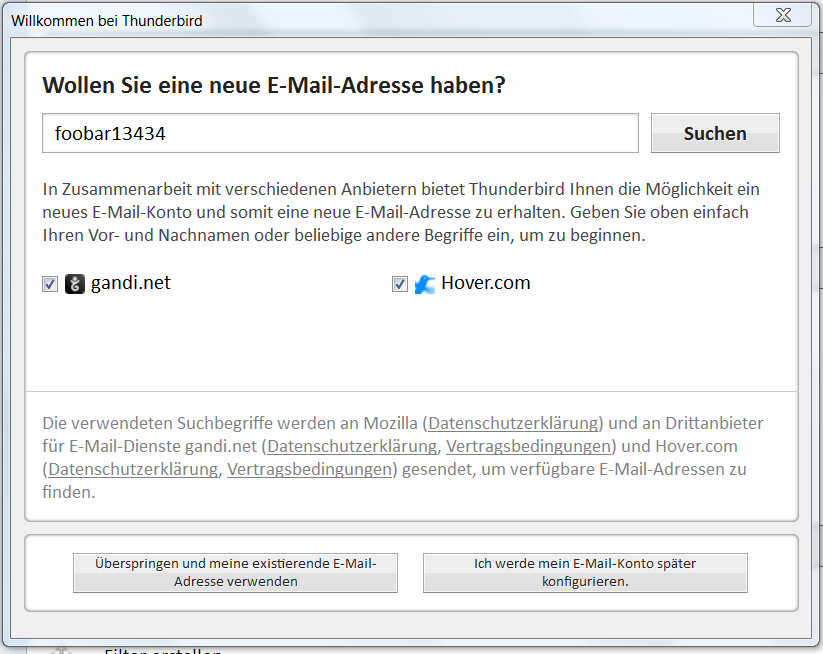
Since we do not want to use a new email address, we have to pay for but our already existing free account at Yahoo! Mail, Gmail, Gmx, Web.de, etc. we click at
![]()
(Means : Skip and use my already existing Email-Address)
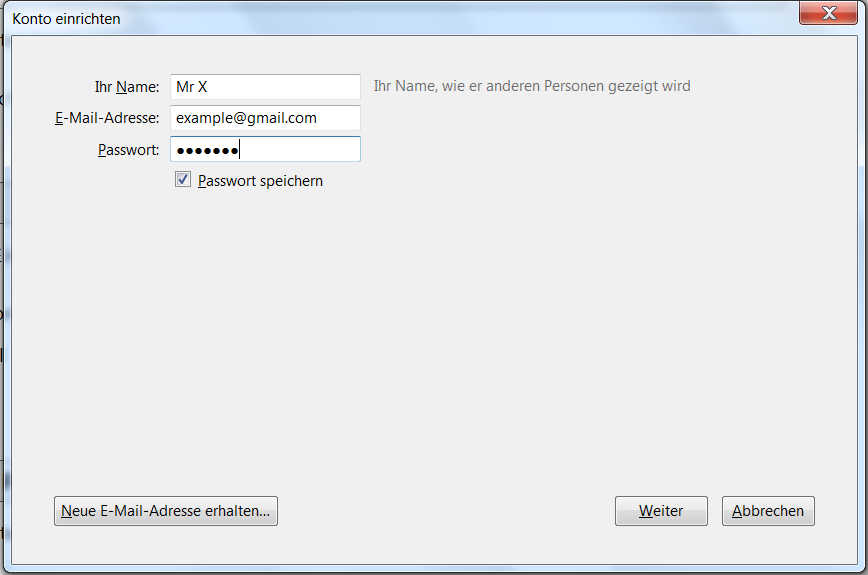
Now we have to enter name, email-address, password for your email host and click next.
Thunderbird will now determine the correct settings for us.
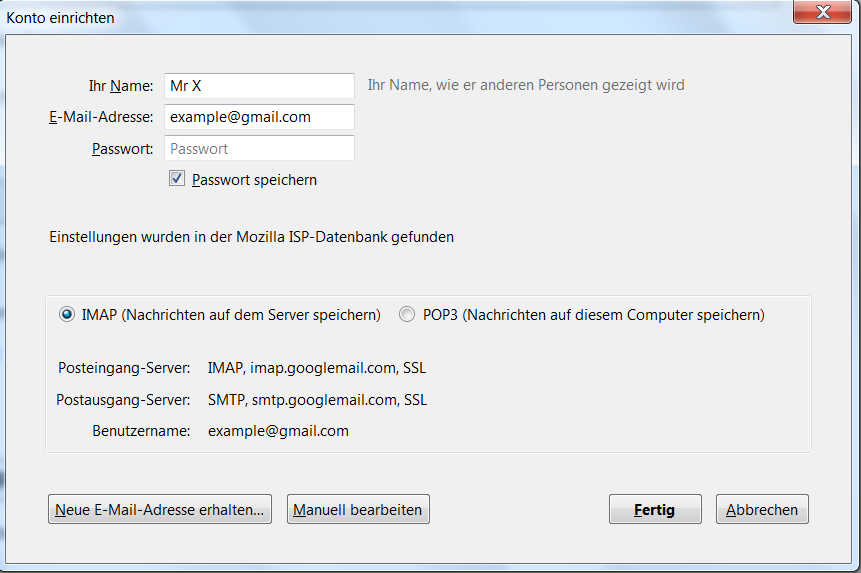
Click Done
Short details about IMAP and POP:
The Internet Message Access Protocol (IMAP) : Messages are downloaded for each direct request for opening an e-mail. Your message list gets synced by downloading the headers of the messages. Your Advantage : Data and Folders(Inbox, Trash, Sent,etc.) remain on your Server and you can access them from all over the world. With Thunderbird, you got the option to completely synchronize folders and subfolders to work offline with your messages.
The Post Office Protocol (POP) : All Folders and Data remains on the local computer where you downloaded the messages to. You can also configure Thunderbird to let a copy remained at your server, but usually it gets deleted at the server if you synchronize your messages. The disadvantage: You cannot access any message from any computer. So it is hard to continue working with your emails, if you have to access your mailbox from a public terminal, for instance.
2.2 Install The Enigmail Add-on - this is not needed if you already installed it by your package manager:
Click at extended options(upper corner to the right) => Add-Ons. Now type in enigmail at the searchbox and execute the search. By clicking install, we are installing Enigmail.
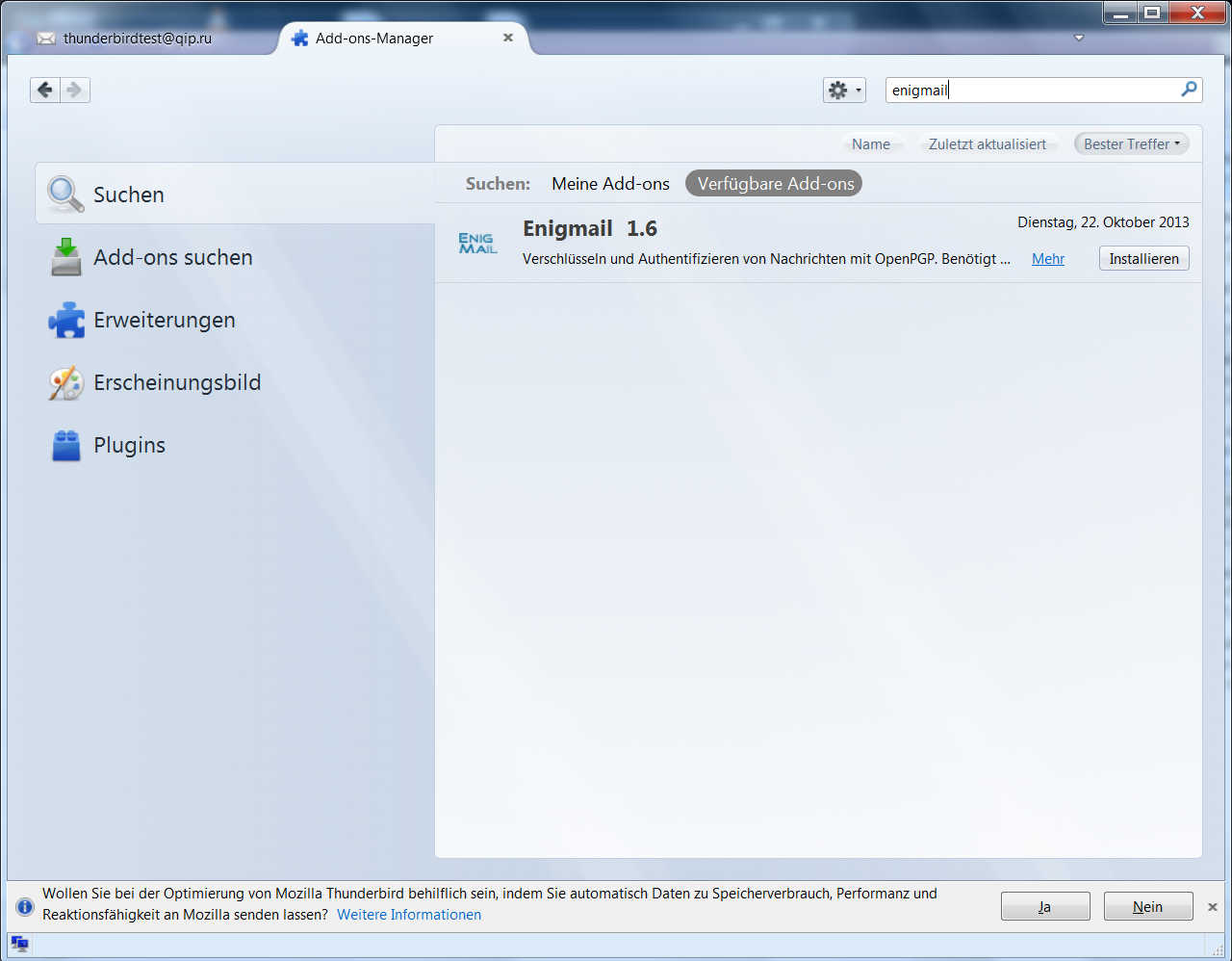
2.3 Configure Thunderbird:
If you already generated the key by command line, you can skip the following step.
2.3.1. Generate a PGP Key with Thunderbird.
First click at extended options(upper corner to the right) and then choose the sub menu Key Management. Now click the option the right Generate/Create and select new key pair.
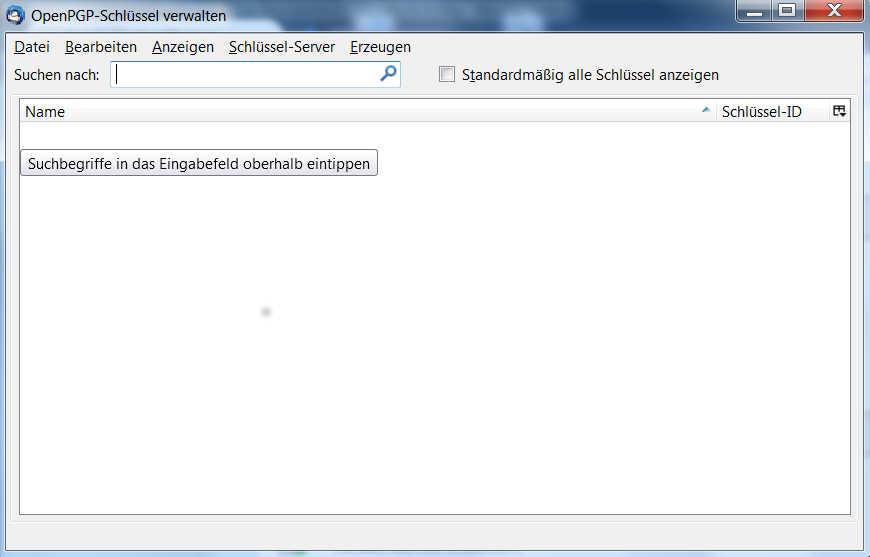
Now we need to enter and acknowledge the password which we are asked for when we want to sign/encrypt/decrypt messages. Validity period is by default 1 year.
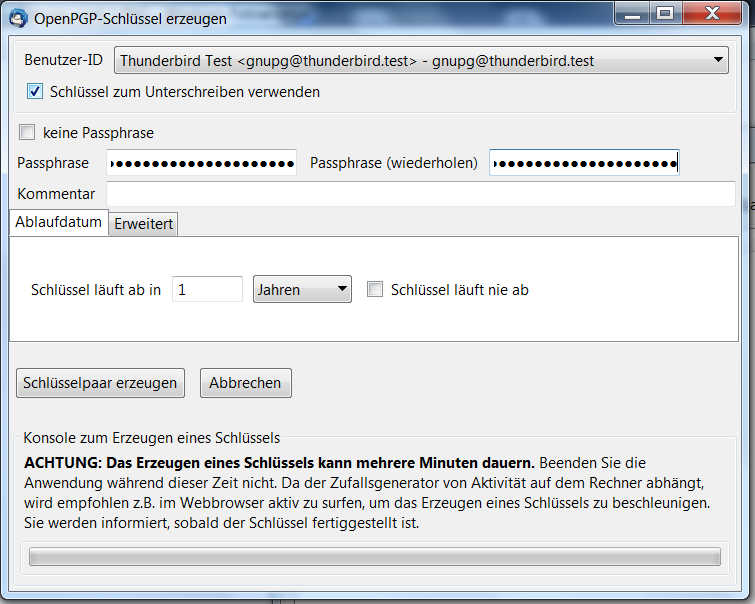
By default, the key strength is set to 2048Bit. I recommend ensuring it's set to 4096 Bit.
Clicking at generate/create key pair will start the key generation.

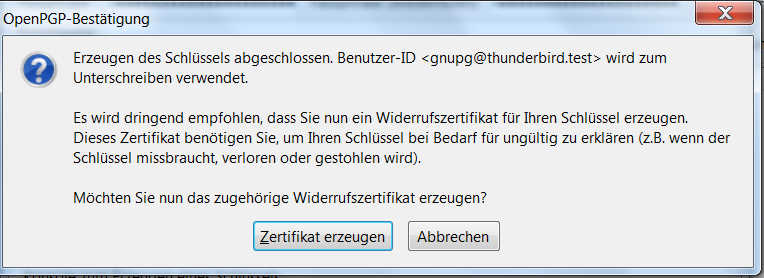
After creating the key pair we should create a revoke certificate to be able to revoke the key anytime, if it got lost or otherwise compromised. You should store this at a save place (extended hd/flashcard/etc.).
To secure the accessibility of your keychains, you need to enter your passphrase from time to time.
2.3.2 checking the existing key pair: extended options => OpenPGP => Key Management
If you can look up your email address nothing has gone wrong.
2.3.3. Setting up PGP for your email-account :
With clicking at OpenPGP - Security, we can configure PGP.
Activate OpenPGP by clicking Activate Open-PGP Support for this Identity. You can use your Email to identify your Key or select in manually.
By activating signing of messages for encrypted and normal messages automatically, any message will be signed, so your friends can authenticate your messages as original.
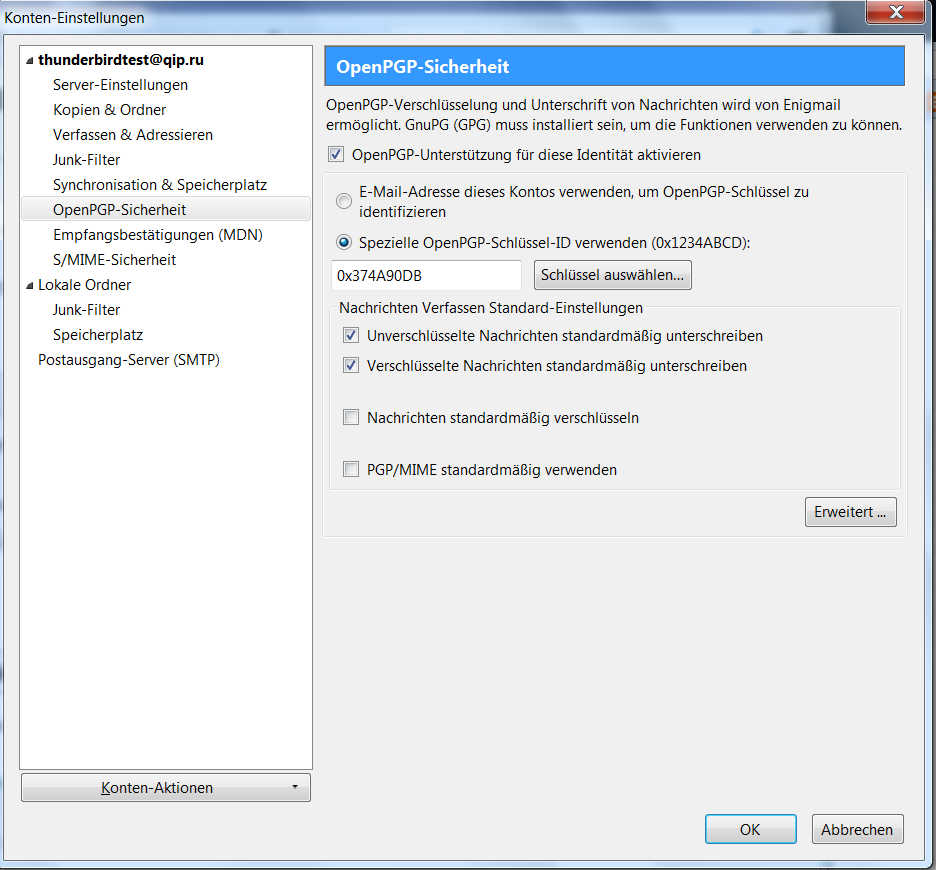
Then click Extended...on the lower corner to the right.
This will open up the following dialog:
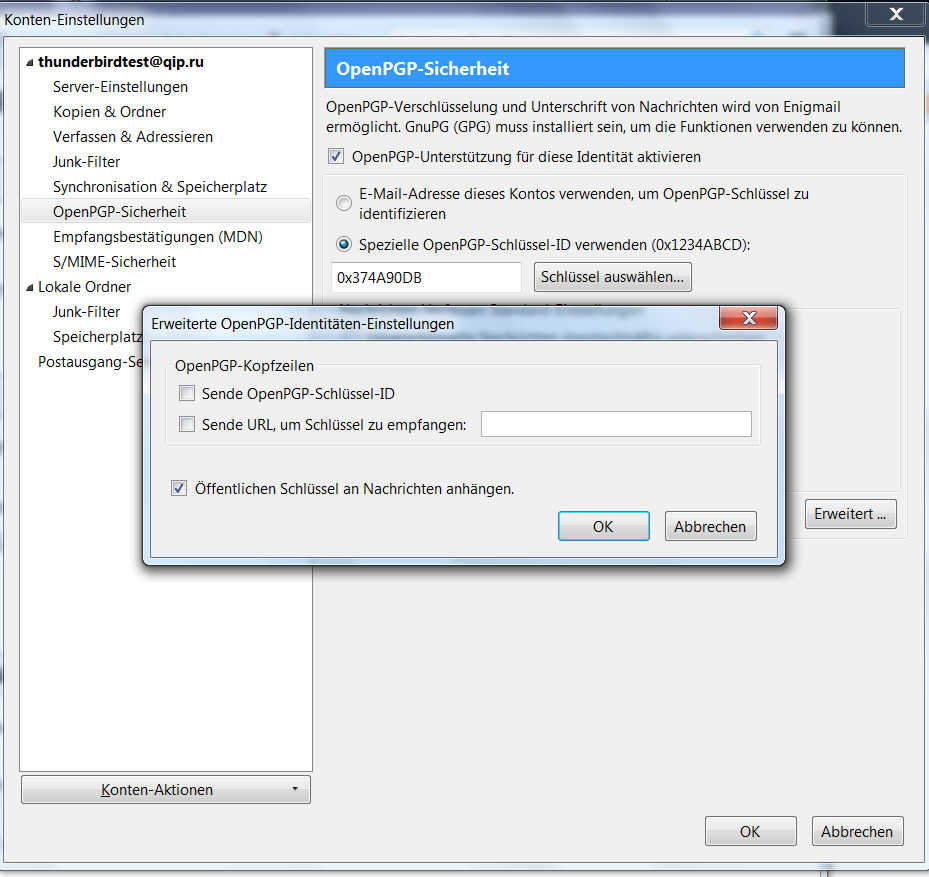
Check the box at attach public key to messages to ensure your new generated public key is sent with your messages so your recipients are able to sent encrypted messages to your address. Your contact needs to import this public key to be able to send encrypted messages to your email-address.
2.3.4. Sending Emails with Thunderbird
If we followed all steps, we can test if the encryption is working: Just open up a new message dialog, enter your own email-address as recipient, enter a topic, choose encryption and signing, type in a message and click send. You now need to type in your key pair passphrase to sign and encrypt the message.
The email you have just received, you can now decrypt by giving your passphrase.
Commonly, your email scenarios will look like this:
A wants to send B an encrypted message : so A needs to import first B's public key.
B wants to send A an encrypted message : so B needs to import first A's public key.
As you see, you need to exchange your public keys first to have a save talk by PGP encrypted e-mails.
Since we configured to automatically attach the public key to any message sent, you just need to email your contacts.
All they need to do is importing your public key by using the Key Management Menu or the command line tools as described before.
[--will be updated--]
Never share your private key !!!
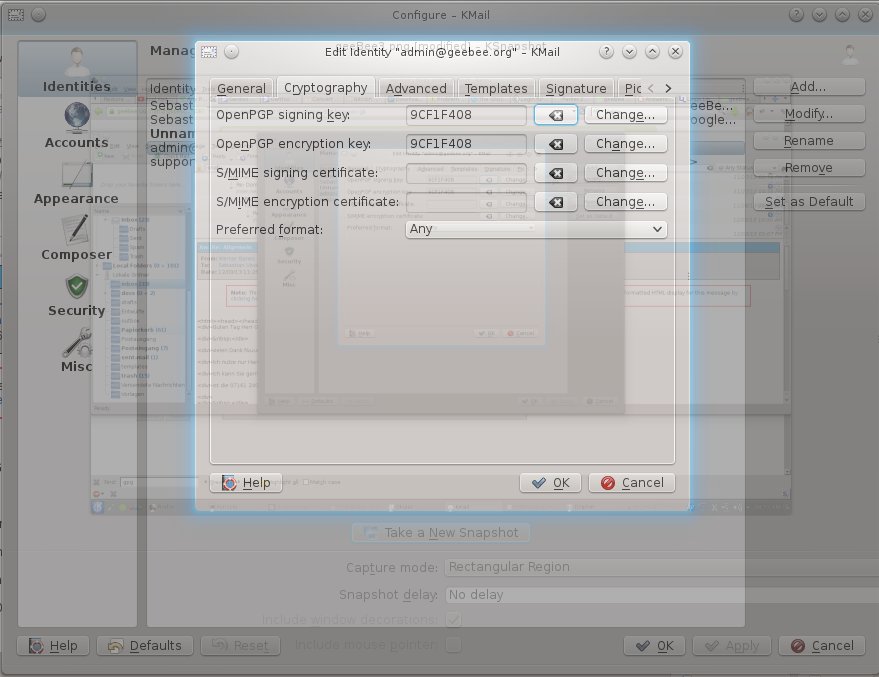
By selecting Settings => Configure Kmail... you can configure your identities:
Choose your generated Key for signing and encryption.
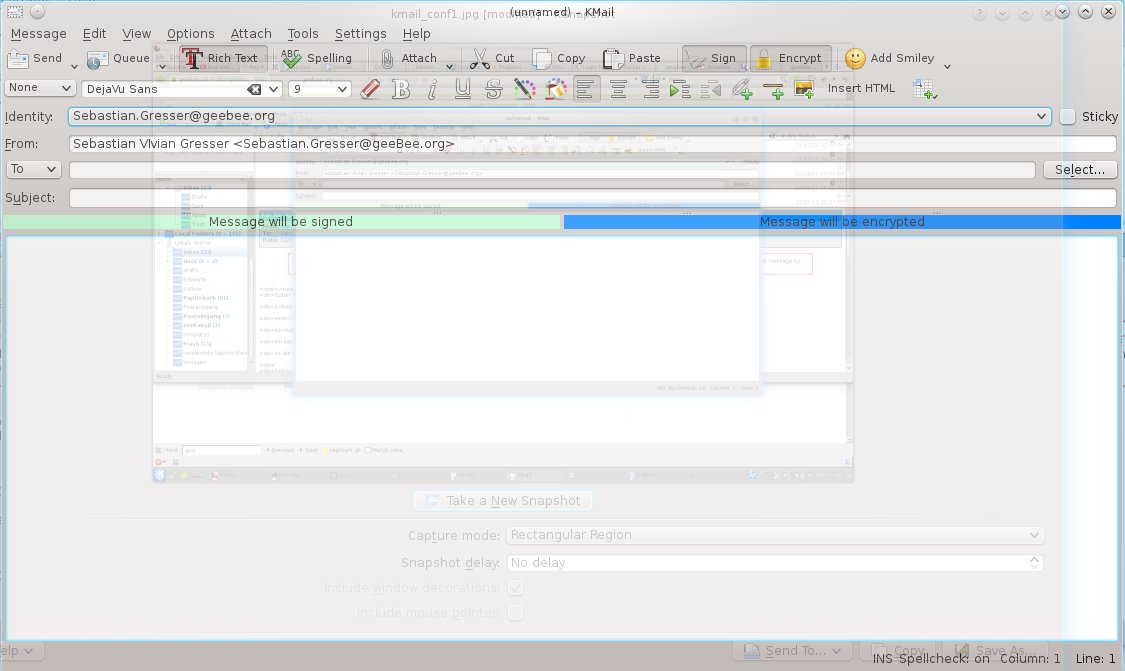
With creating a new Email, you have now the options to Sign and Encrypt. Encrypt is working if you have already imported your friend's public key and signed it as trusted.
Have Fun with your pretty good privacy! ;)
Posted at 2014-04-30 21:31:16( updated at 2018-09-17 22:26:53 )
in Manuals
Tags:
